
Kademlia Dht Network Implementation Nodes Bitcoinwiki

File System Implementation Ppt Download
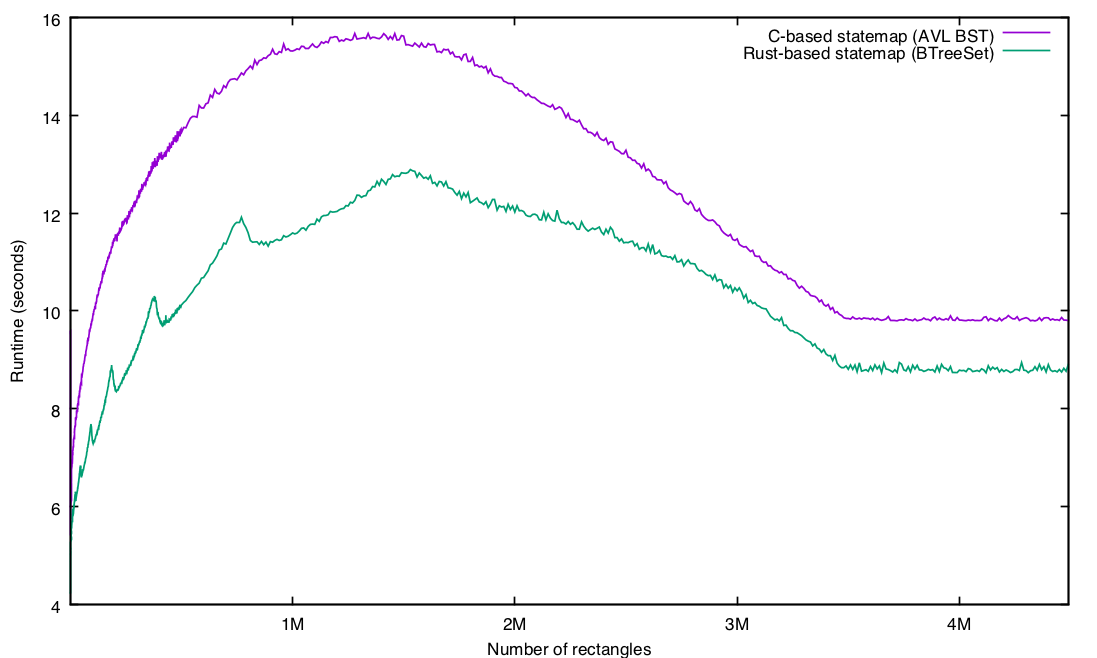
The Observation Deck The Relative Performance Of C And Rust
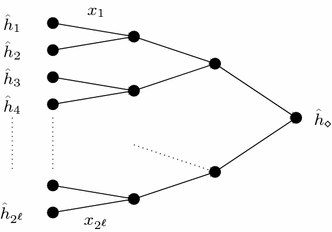
New Second Preimage Attacks On Hash Functions Springerlink

Hierarchical Voxel Block Hashing For Efficient Integration

Bellow Press Latest Editions Of Business Of Furniture And
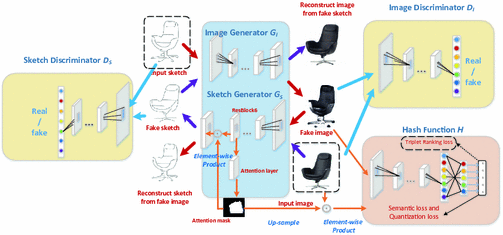
Generative Domain Migration Hashing For Sketch To Image

Bellow Press Latest Editions Of Business Of Furniture And

Blockchain Research Bytes 1 Horizon Globex Medium

How Blockchain Technology Works Guide For Beginners

Bishop On Twitter Once Again Thank You Ncakenya For

Bitcoin Hashrate Ai Massimi Storici Superati Gli 80

Caching In Python

Hierarchical Voxel Block Hashing For Efficient Integration
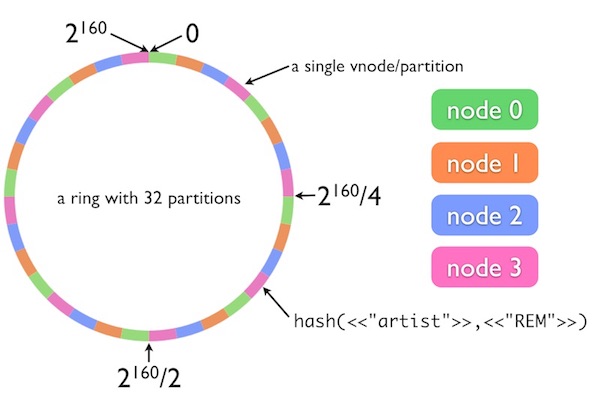
A Critique Of Resizable Hash Tables Riak Core Random Slicing
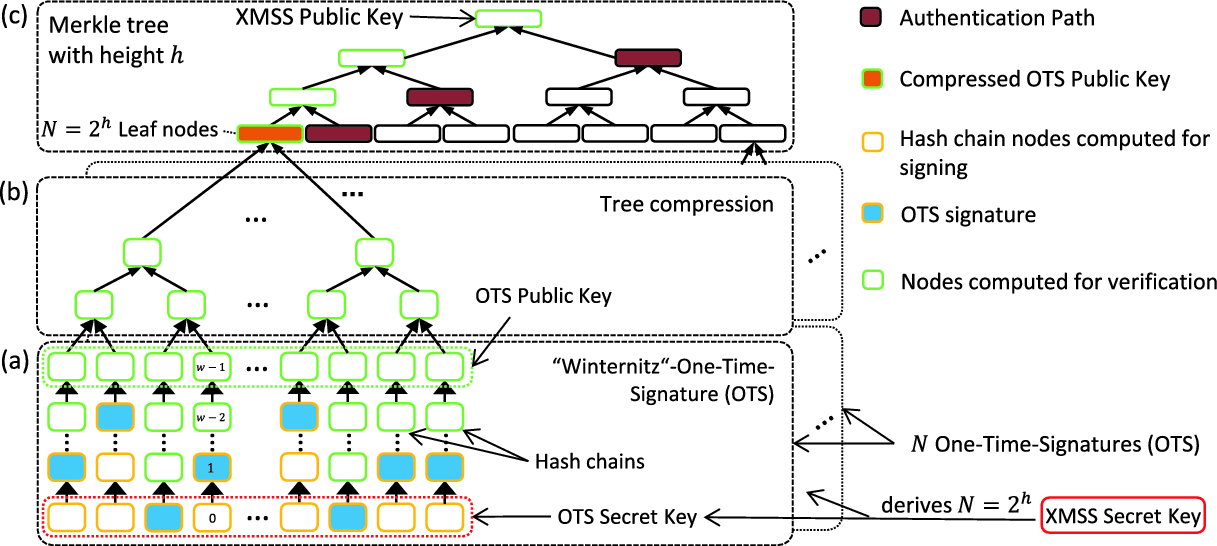
A Latency Optimized Hash Based Digital Signature Accelerator

Leadership At Horatio Elementary Oie Blog

Get Up Amazon De James A Levine Fremdsprachige Bucher
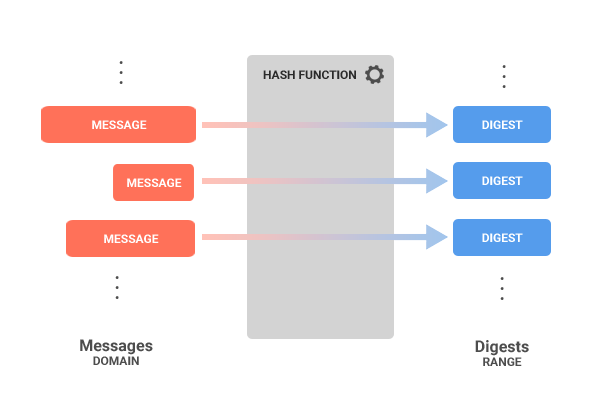
What Is A Digital Signature Dzone Security

Becausejenjonessaidso Hash Tags Deskgram

Lean Manufacturing Consultants In Chennai Hash Management
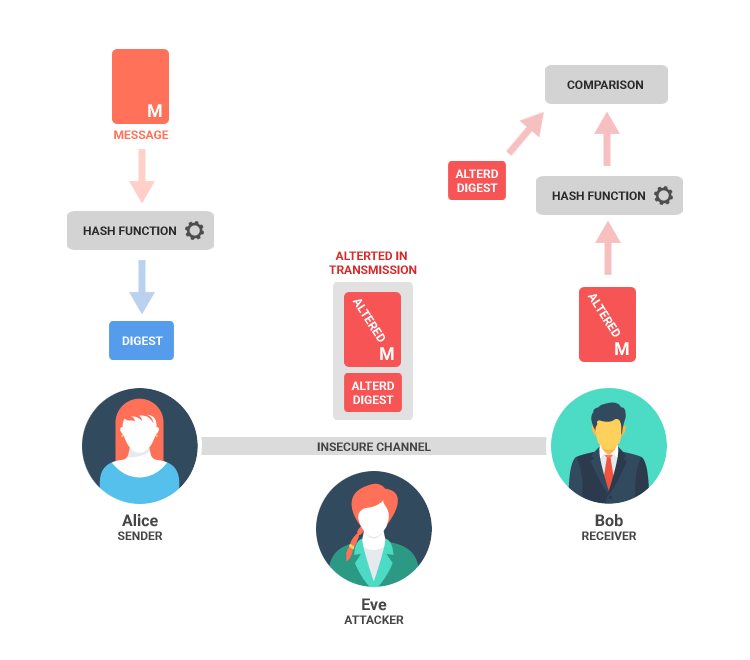
What Is A Digital Signature Dzone Security

How To Prevent Cybercrime 9 Helpful Tips Hashed Out By
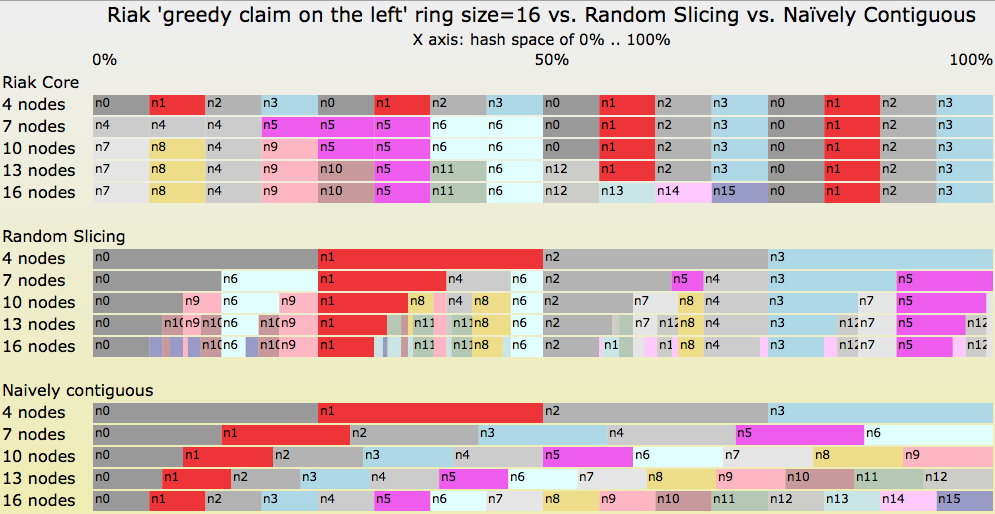
A Critique Of Resizable Hash Tables Riak Core Random Slicing

Hash Tables In C With The Djb2 Algorithm The Startup

Interhash Interhash And Interhash Council

Spring Security Authentication Using Locally Stored H2

Data Organization In Bucket Chained And Cuckoo Hash Tables

Kademlia Dht Network Implementation Nodes Bitcoinwiki

Dr Med Dent Momtchil Mehandjiev Donauzahnarzt 4310 Mauthausen
Implementing A Merkle Tree In Javascript Salma Sultana

Pdf The Impact Of Md5 File Hash Collisions On Digital

Top 10 Liberal Arts Skills You Need To Succeed In Tech

Chameleon Hashes With Dual Long Term Trapdoors And Their

Noise Removal Using Median Filter In C Geeksforgeeks

Finding Similar Images Using Deep Learning And Locality
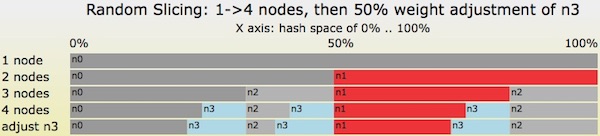
A Critique Of Resizable Hash Tables Riak Core Random Slicing

Finding Similar Images Using Deep Learning And Locality

Westunes Vol 54 No 1 Jan Feb 2004 By Far Western District

Bellow Press Latest Editions Of Business Of Furniture And

How To Prepare For A Technical Interview Tips And Tricks
Bellow Press Latest Editions Of Business Of Furniture And

Datenschutz Frauenzimmer

Symbol Tables

Program To Print The Berth Of Given Railway Seat Number

Data Organization In Bucket Chained And Cuckoo Hash Tables

Bellow Press Latest Editions Of Business Of Furniture And

What Is A Bitcoin Hash And Sha 256

Arbeiten Bei Itemis Produktmanager Standort Und

Bellow Press Latest Editions Of Business Of Furniture And

Iota And Cybercrypt Announce New Lightweight Trinary

Arbeiten Bei Itemis Feel Good Manager In Hamburg

Circular Queue Set 2 Circular Linked List Implementation

Consistent Hashing In Your Python Applications

New John Lewis Chair Will Bring Fresh Outlook News Drapers

Impact Of Hash Value Truncation On Id Anonymity In Wireless

Practical Cryptography Algorithms And Implementations Using C

Zobrist Hashing Chessprogramming Wiki

Daniel J Bernstein Hashbreaker Twitter

Javascript Data Structures Tutorial Learn Its Types And
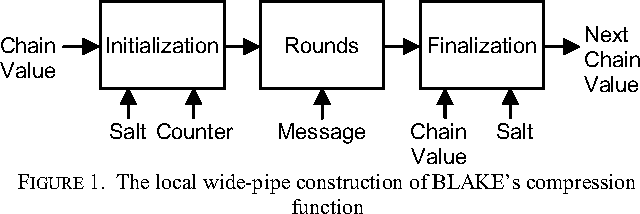
High Throughput Hardware Implementation Of Secure Hash

Institut D Electronique Et De Telecommunications De Rennes

Behorden Spiegel Marz 2019 By Propress Issuu

Javascript Data Structures Tutorial Learn Its Types And

Secure Coding Technique Avoiding Username Enumeration

Symbol Tables

Ppt Statistical And Performance Analysis Of Sha 3 Hash

Organisations Must Prepare For Cyber Breaches As If Already
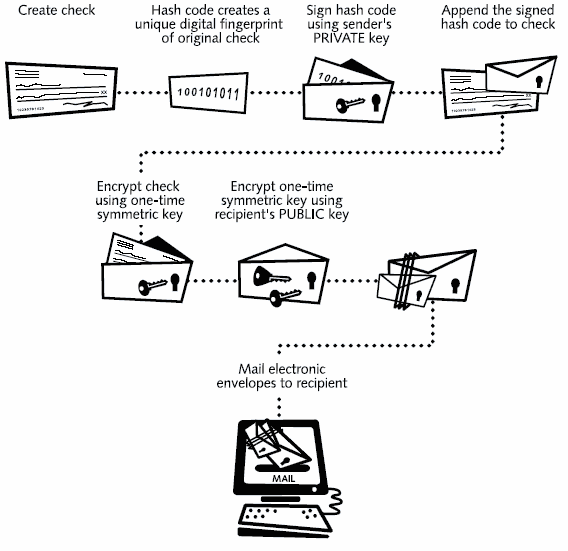
Net Encryption Simplified Codeproject

Updated Leaders Of Proposed Salmonberry Trail Between

Hashtag Analytics 27 Actionable Hashtag Strategies Keyhole
How To Safely Store Your Users Passwords In 2016 Paragon

The Weekly Hash September 2 6 Kraken Blog

Pscc Parallel Self Collision Culling With Spatial Hashing

Weworc Western European Workshop On Research In Cryptology

A Critique Of Resizable Hash Tables Riak Core Random Slicing

Lxcloud Cr Towards Linux Containers Distributed Hash Table

A New Fast Hash Table In Response To Google S New Fast Hash
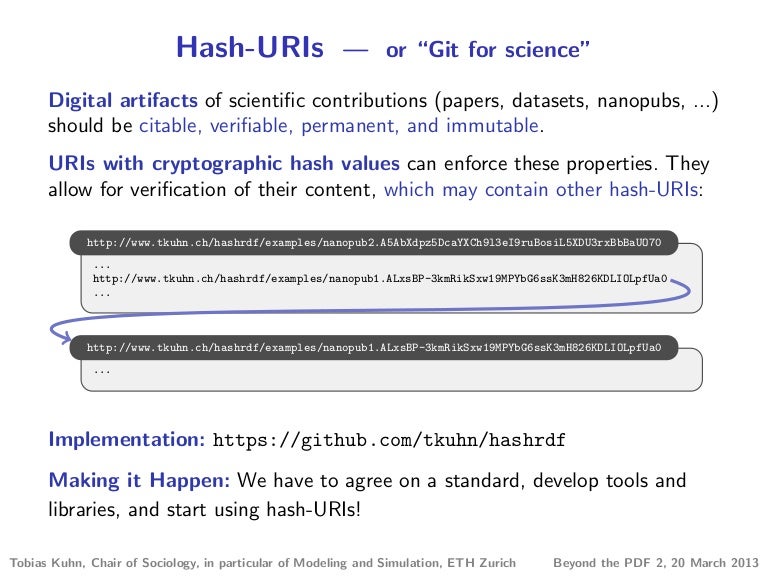
Hash Uris Or Git For Science

Dlt Pisa 2019

Bafinperspektiven Ausgabe 1 2018

Pdf Chameleon Hashes With Ephemeral Trapdoors

Ipv6 Flow Label Misuse In Hashing Ripe Labs

How To Understand Locality Sensitive Hashing Stack Overflow
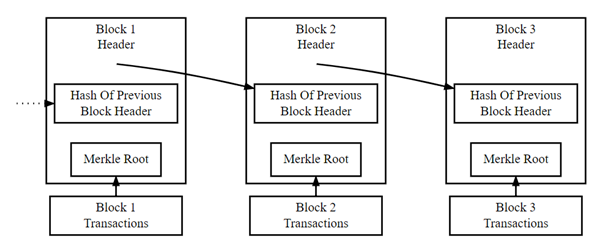
Beginners Guide To Blockchain Technology Part 2 Dzone

Collision Based Hashing Algorithm Disclosure Dzone Security
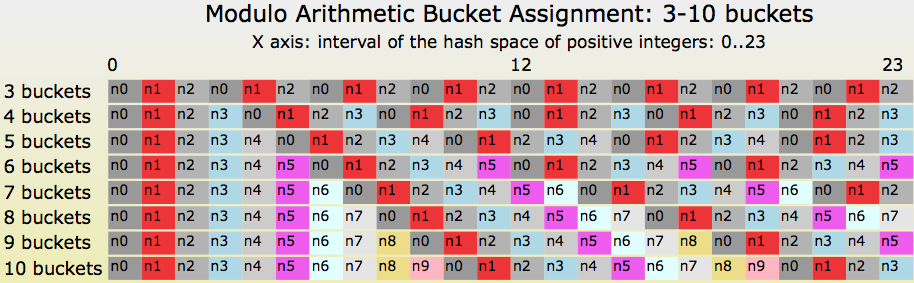
A Critique Of Resizable Hash Tables Riak Core Random Slicing

6 Index Types In Postgresql 10 You Should Know Packt Hub

Demo How To Create An Md5 Hash Micro Focus Community
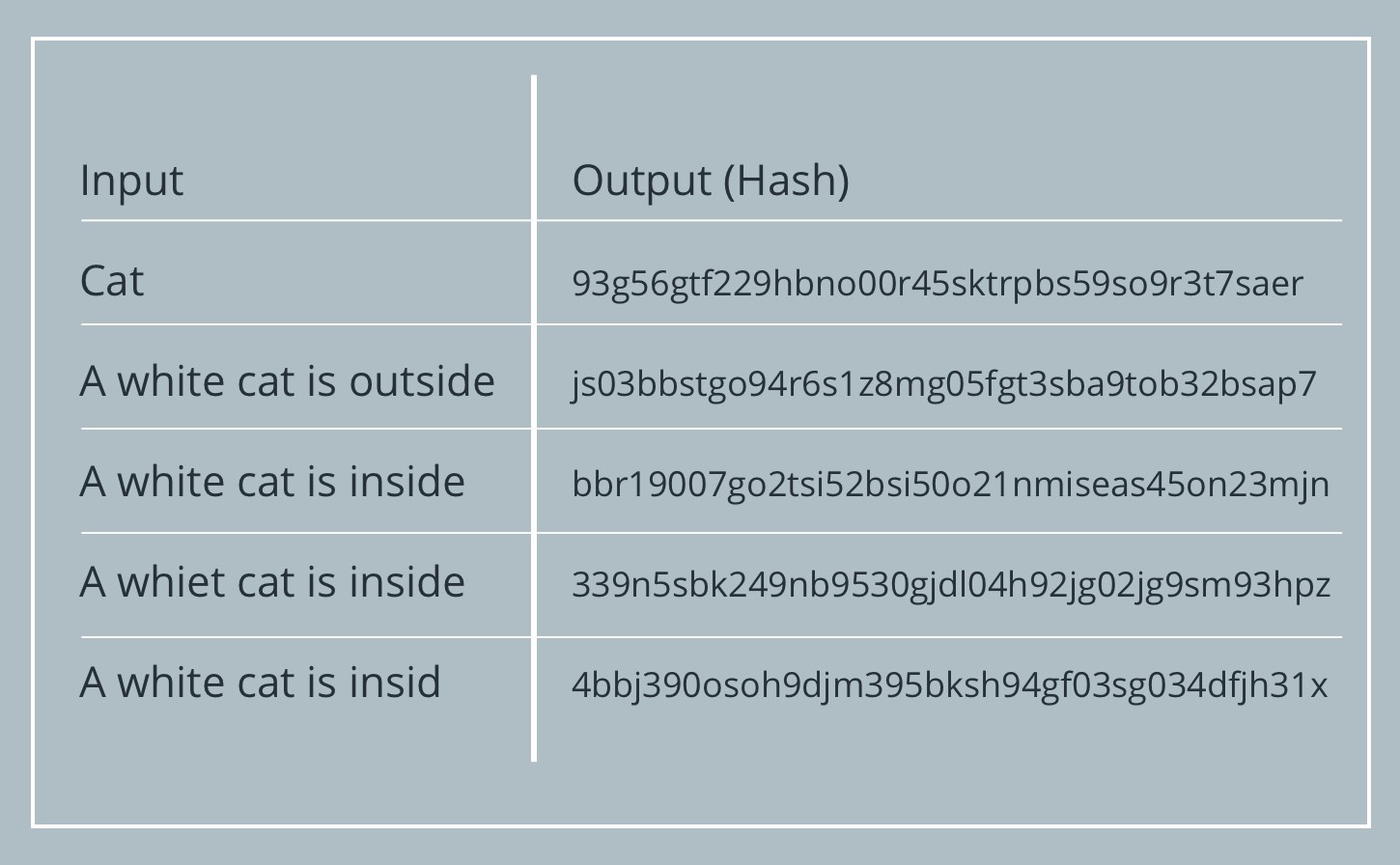
How Blockchain Technology Works Guide For Beginners

Cryptologie

Bitcoin Transaction Block Chains Video Khan Academy

Collaborating Across Departments To Achieve Vision Zero

Hierarchical Voxel Block Hashing For Efficient Integration

Lean Manufacturing Consultants In Chennai Hash Management

Bellow Press Latest Editions Of Business Of Furniture And

1 Hashing Introduction Dictionary A Dynamic Set That
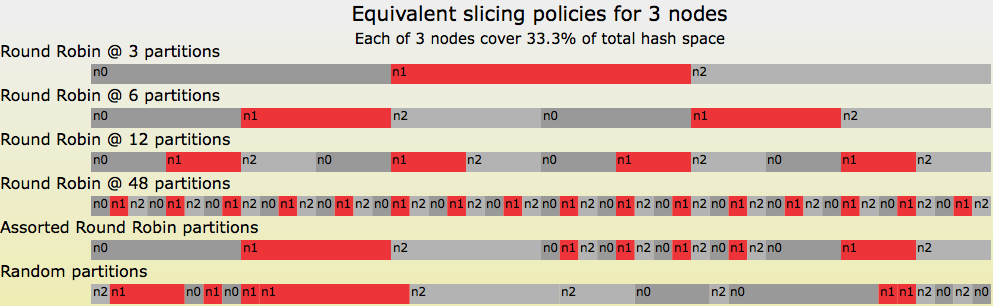
A Critique Of Resizable Hash Tables Riak Core Random Slicing

